Authors: Micah Lahren
Most businesses that work with sensitive data and have multiple workstations or servers also make use of alarm systems and theft protection services in case of attempted theft. However, many businesses are growing exponentially and constantly send out traveling representatives to do demonstrations or make business contacts. Others are of a mobile nature and require constant travel, often with devices containing the materials for the demonstrations or other sensitive data such as trade secrets or promotional information. As users of mobile devices increase, and dependence on them increases, the loss or theft of such devices are becoming increasingly common, not to mention costly. In some cases, the actual value of the device stolen may be chump change compared with the value of the information on the device and the disruption to business operations. How can you protect your tech clients from device theft, information theft from their device, and potentially assist in recovery of their device?
There have been several anti-theft solutions floating around for some years, some of them paid services, others completely free but offering limited features, while some only offer a 30 day trial period. One service that stands head and shoulders above the rest while maintaining free and open source status is known as Prey. While offering a free service, they offer ‘Pro’ services for an exceptionally reasonable cost, which include more features as well as a higher degree of service. All ‘Pro’ plans contain the same extra features, but are based on how many computers your client wants to track with that one account.
If you are worried that Prey won’t work on your client’s device, have no fear. Prey can be installed on Windows, Mac, Linux, Android, iOS, and even has a specialized version for Ubuntu. While there are other free solutions for Android and iOS, which I’ll refer to later, it can’t hurt to have more than one in case one of the theft protection solutions is detected by the thief, and disabled. With multi-platform support like this, your client can track a laptop, smartphone, and tablet, all from one account. The free version offers 10 reports per device, WiFi and GPS geolocation services, and offers data protection features such as onscreen remote alerts, lockdown, alarm triggers, and will wipe sensitive data from the device if your client chooses that feature.
The ‘Pro’ versions include 100 reports per device, on-demand activation, report frequency at a rate of up to one report every 2 minutes, and keeps a record of your client’s device checking in periodically. It scans your client’s device hardware for changes, and automatically updates by remote. Included in the many features mentioned is access to automated installers which make installing on multiple devices much easier, bypassing the need to manually set them all up one by one.
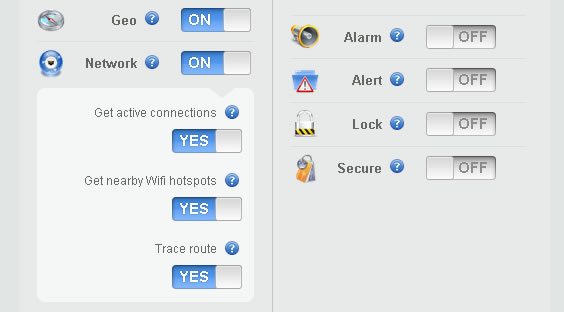
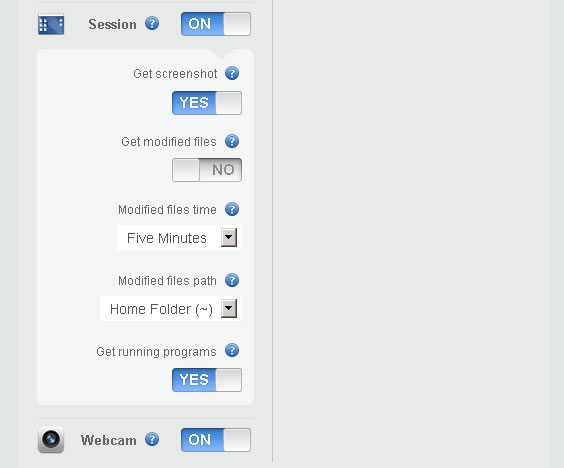
What do the reports include? The Geolocation feature will show your client where on the map their device is, down to the exact coordinates on a Google Map capture. The Network feature will detect nearby networks and detect location based on nearby networks, hotspots, active connections, and a trace route. The Session feature gets a screenshot of what the thief is doing on the device, notifies you of modified files, and running programs. Last in the free service list of features is the Webcam option, which takes stealthy pictures of the thief at the stolen device.
One warning about the webcam feature on devices with little lights that turn on when the webcam starts up: this may notify the thief that the device is taking pictures, and it may alert them to the fact they are being tracked. On the other hand, the short time the light actually turns on is not very noticeable, unless you’re actually looking for it and know what’s taking place. The average thief will probably not notice or may not realize what the light signifies, allowing your client to track their ‘prey’ unnoticed.
Unfortunately, there seems to be a slight problem with Ubuntu 12.04 taking screenshots of what’s going on, on the screen, when the device is reported missing. I’m sure this will be patched up soon, and while that feature seems to be an issue at the moment, the rest of the report is more than sufficient to track the stolen device down. The screenshot feature may be useful in case the thief tries to log into a social network that displays their name or other personally identifiable information, but may not always be useful in recovery. All in all, for a free service with all those great features, I heartily recommend it to you for protecting your clients from device theft.
There are other solutions for specific platforms, but they are limited in functionality. For example, ‘Find My iPhone’ enables you to find your missing iPhone, iPad, iPod touch, or Mac, display a message, play a sound, remotely lock it, or erase data on it, but only if you access the app from another iOS device. If your client loses their iPhone and doesn’t have another iOS device, hopefully they can find a friend that does, or they might have a problem.
Another handy app for Android devices is called Android Lost. It can read the latest SMS messages from the device and send them to an email address, activate a remote control alarm, view the device location on a map, lock it, and even send SMS messages from a PC to the device. Remote messages can be sent to the device in case some friendly soul has located the device and wishes to return it. On the other hand, the device may contain sensitive data, and the device can be wiped of all SMS data, contacts, and Google setup configurations. Calls can be forwarded, the SD card can be erased, notifications of SIM card changes will be sent via email, and a list of all incoming and outgoing calls will be sent to the owner of the device as well. The camera can also be utilized for taking pictures of the thief, and the phone can still be accessed and data retrieved via the internet. Multiple phones can be used on the same account, and from all the features, you can see why this app is very useful for protecting your clients from device theft.
Some of us have never had our devices stolen, and we’ve never given it a second thought, until a fellow Tech or workmate has lost their device or had it stolen, or a client comes in to get a new device because their device has been lost or stolen. It’s imperative to take preventive measures before the chance becomes reality, and protecting your clients from device theft is an important measure of security in the Tech sector that shouldn’t be neglected.
© Technibble – A Resource for Computer Technicians to start or improve their Computer Business
To get started with your own computer business, check out our Computer Business Kit.